I've been using Prowler for a few years now. It's my go-to open-source tool for quick cloud security audits.
A few months ago, Prowler released v5 (codename Powerslave) at AWS re:Invent. The new dashboard in the release blog looked cool. However, I was busy with my LLM experiments.
Last week, I had time to play around with the latest Prowler release. Here's my analysis.
To summarize Prowler v5, it's Prowler's big leap from being an open-source CSPM tool to a self-hostable open-source CSPM platform.
It has structured its code a bit. It has a much fancier dashboard as part of the Prowler App. It also exposes APIs so you can access Prowler App programmatically.
But before we dive deeper, let's look at some pain points that Prowler App in v5 solves.
Limitations with the predecessor (v4)
Minimal Dashboard
Prowler v4 has a minimal dashboard that you can spin up using the command prowler dashboard.
(Just FYI, the Prowler dashboard feature is still available in v5)
Prowler Dashboard
It's better than having no dashboard at all. However, the minimal dashboard is more of a temporary HTTP server that can quickly visualize findings than a full-fledged standalone web server.
It displays the findings from the saved CSV files from previous scans.
One thing to note is that the dashboard doesn't have any authentication. So, even if you write a wrapper on top of the Prowler dashboard to host it as a server, then be careful - it might be a single misconfiguration away from becoming publicly accessible to the internet.
Periodic Scans & Tracking Changes
Out of the box, v4 doesn't support periodic scans. To achieve it, you must create a Linux cron or something similar.
If you have set it up, congrats. Now comes the operational part.
With periodic scanning in place, you need at least periodic validation of these findings. Now,
How do you know the diff between two scans?
How do you know which findings got closed and which popped up?
How do you only send alerts to your Slack/Microsoft Teams when new issues are detected?
It's tricky.
You need to write custom scripts to achieve those tasks.
If you don't want to write custom scripts, you can achieve it by connecting Prowler to AWS Security Hub and integrating AWS Chatbot to alert new findings on Slack/Microsoft Teams. I've described the process in my course.
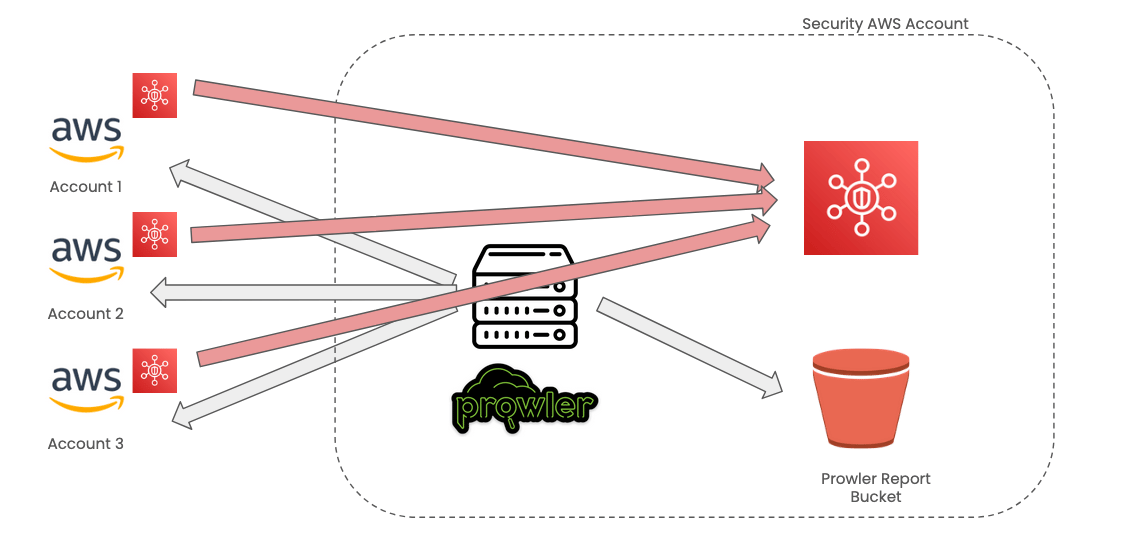
Slide from my course on sending Prowler alerts to Security Hub
Again, using Security Hub solely for detecting and alerting on the diff purpose might not be very appropriate.
Welcoming Powerslave (v5)
Prowler v5 tackles both the above limitations using the Prowler App - a full-fledged CSPM platform, in my opinion.
(Note: If you stick with the v5 CLI, the problems mentioned earlier will persist.)
Unlike the dashboard feature, which you can spin up with just the prowler dashboard command, the Prowler App is a multi-container docker-compose file you'll need to download and setup.
curl -LO https://raw.githubusercontent.com/prowler-cloud/prowler/refs/heads/master/docker-compose.yml
curl -LO https://raw.githubusercontent.com/prowler-cloud/prowler/refs/heads/master/.env
docker compose up -d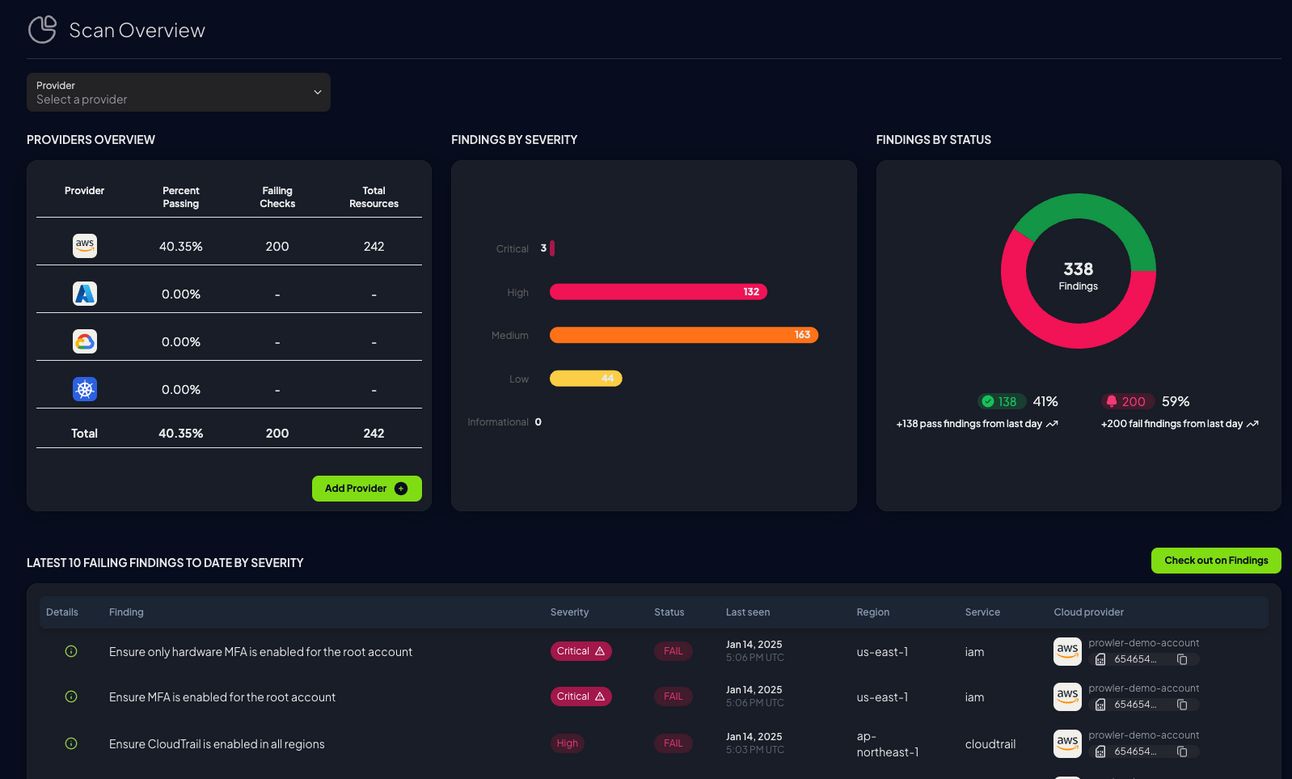
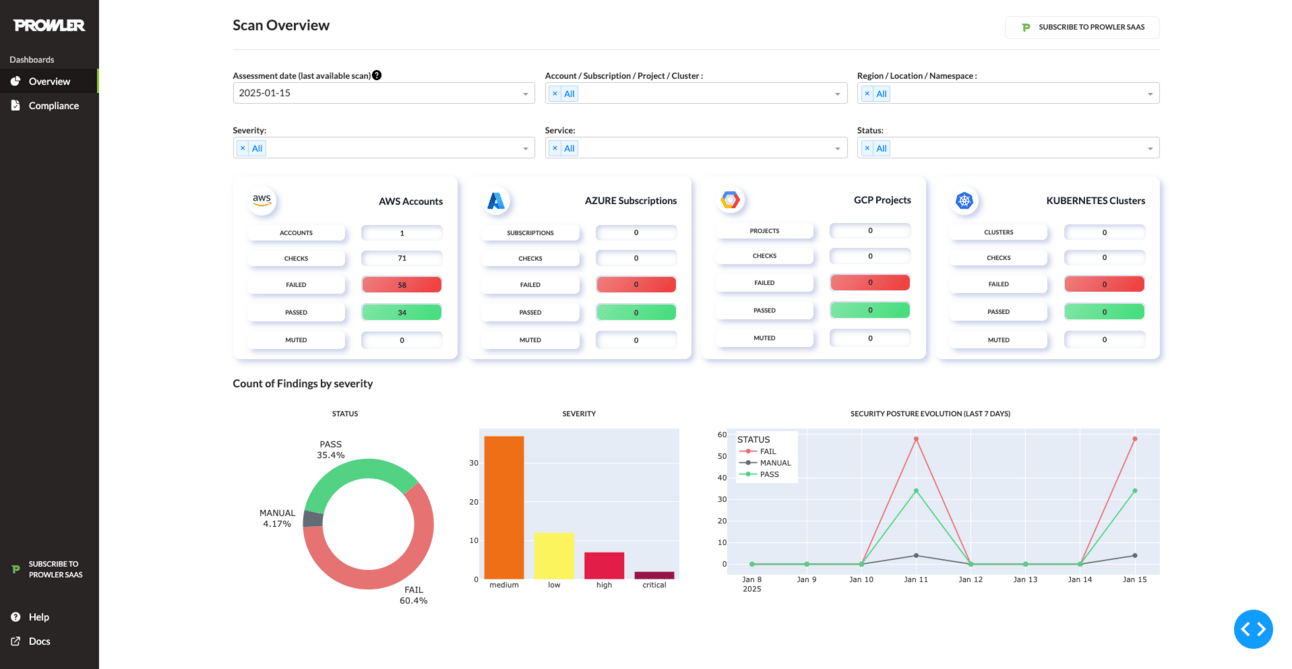
Prowler App Dashboard
You can self-host it. Connect your cloud accounts & Kubernetes clusters to it. Start scanning and securing.
Features of Prowler App:
Supports multi-user and RBAC - Adds authentication and authorization layer view findings or manage settings. Users can be assigned roles. (SSO Connectors that are currently on their roadmap will be a great feature if released to OSS Prowler)
Pretty good dashboard - Filters out findings based on accounts and scan IDs, check your compliance status against multiple frameworks, etc
Stores the findings in Postgres DB - Interacting with the DB is unnecessary, but if you're into connecting data to BI tools in your org, this can help you.
Periodic scanning and diff between scans out of the box - Once you connect your cloud accounts and initiate a scan, it will automatically be configured to scan every 24 hours. You also have a filter to find the delta between scans.
Documented APIs to interact - If you have any use case where you need to interact with Prowler findings programmatically, then APIs can be the way to go.
Supports dark mode - If you're into switching on dark modes across the apps you use, then this is for you 😛

Prowler App’s Delta Feature

Prowler App’s Compliance Dashboard
Should You Upgrade?
Well, if you use Prowler CLI, I highly recommend to upgrade. You have new checks (including GenAI checks), fixers, and bug fixes.
If you want to try the Prowler App, you don’t need to upgrade your CLI. You can download the docker-compose file and set up the app.
If you are trying out the Prowler App, I need to make you aware of the following:
You can't onboard all your AWS accounts under AWS Organization at once. Instead, you have to connect one account at a time.
The option to export the findings is not available. The same goes for options to mute or mark as false positive.
You can't change the scanning schedule—a fixed schedule of 24 hours per account.
Anyone who can access the app can sign up for an account. There is no option to turn off that feature.
The default configuration scans across all your AWS regions. It doesn't support mutelists on the UI yet.
Doesn’t support sending alerts to Slack/Microsoft Teams.
Prowler App containers (especially the Django container) are resource-hungry. The CPU spiked up to 200% during the initialization, and the containers used 4GB of RAM on my Macbook. The CPU usage dropped once the initialization completed, but RAM was hovering above the 3GB mark.
Most issues I mentioned are on Prowler's roadmap or are actively being fixed.
I predict that Prowler App, in a few releases, will become a robust self-hostable CSPM platform.
Until next time 👋



