Thunder CTF is an open-source cloud security-related CTF that aims to teach about the security of the Google Cloud Platform (GCP).
This CTF has various levels. The player has to find a particular secret in each level, and the location of the secret is stated at the start of each level. The path the player takes to access those secrets stored at different places helps the player learn about possible misconfigurations in the Google Cloud Platform.
Thunder-CTF has six levels:

Source: https://thunder-ctf.cloud/
We will go through all of these levels one by one.
NOTE: To solve all these levels, we will set the project to cloudsecurityclub-dev. Set your project likewise.
Before starting the level, follow the basic setup on the Google Cloud Platform described on the Thunder-CTF website. Then, begin the challenge.
So, without wasting any time. Let’s get our hands dirty, conquer these challenges, and enhance our knowledge about the Google Cloud Platform security
Level 01
Setting up the project first:
gcloud config set project YOURPROJECTID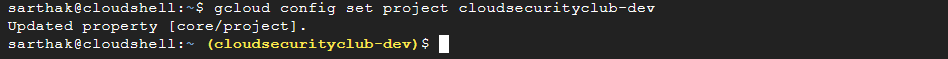
Starting the challenge:
python3 thunder.py create thunder/a1openbucket
This challenge has created a Google Cloud Storage bucket a1-bucket-604989372723.
Let’s look at the contents of the bucket:
gsutil ls
gsutil ls gs://a1-bucket-604989372723/
We can see that this bucket contains the document named secret.txt.
Now, we will copy this secret.txt into the current working directory.
gsutil cp -r gs://a1-bucket-604989372723 .
Using the ls command, we can see that the directory with bucket name is created in the working directory.
ls
Traversing to the bucket directory and listing the content of it:
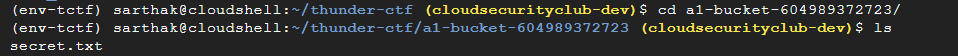
Now showing the content of the secret.txt using:
cat secret.txt
With this, we got the secret value within the storage bucket.
Summary
In this level, we learned from the challenge description that the secret is in the bucket. Following that information, we tried to see if the bucket and its contents were publicly accessible. Accessing the bucket showed a file named secret.txt. Finally, we copied the secret.txt file from the bucket and found the secret.
NOTE: The objects in the bucket are publicly listed but not downloadable. We could copy the bucket’s content using gsutil cp because we are the project’s owner, but anyone other than the owner can’t download the object. I assume Thunder-CTF did this intentionally, so users outside the GCP project couldn’t access the secret file.
If you want to read more about GCP misconfigurations, check out my Thunder CTF Level 2 write-up!

